What is a VPN and How Does It Work?
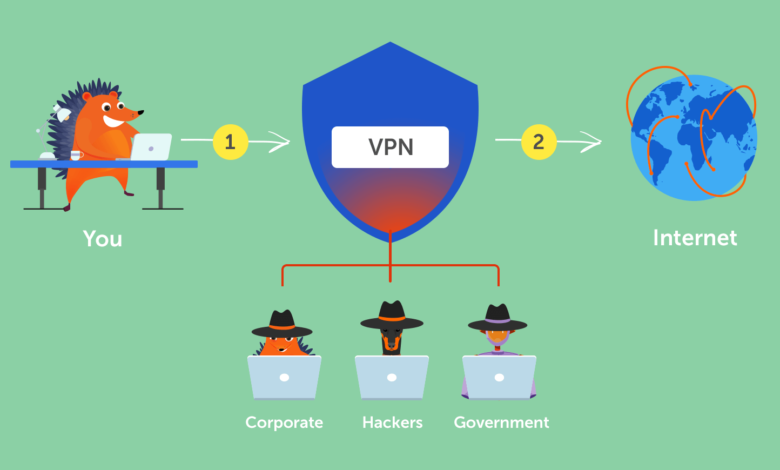
If you’re looking to protect your privacy online, you need to use a vpn Work service. There are several options available, and each has its own security features. These features include encryption, a reliable tunneling protocol, leak protection, and a kill switch. To choose the best VPN for your needs, follow these steps:
Advanced Setup of a VPN
If you’ve just purchased a lesmeilleursvpn and want to set up a connection on your computer, you need to know what to do next. There are many steps involved in this process, but it’s a fairly straightforward process. To start, you need to collect supporting information from your VPN provider, including the server name, region, IP address, and credentials. You may also need to gather some proxy information. Below are some tips for setting up a VPN.
To begin the process, open the VPN settings on your computer and select the proper protocol. Next, you need to specify a name for your VPN connection, enter your username and password, and select your network. After that, you can choose the type of connection, IPsec, or L2TP. Finally, you can add additional information to your VPN connection, including a proxy. For example, if you’re using a proxy, you’ll want to specify a server in the same network as your VPN. Then, tap on the “Advanced setup of a vpn” button.
Open-Source VPN
OpenVPN is a free and open-source VPN Work protocol for connecting to the internet. The protocol has been around for over 20 years, and its developers have worked to adapt it to different platforms and operating systems. OpenVPN is also included in many VPN router firmware projects, including the popular DD-WRT. The developers of OpenVPN have even founded a company called OpenVPN, Inc. to commercialize the technology. OpenVPN offers several products, including the Access Server, a Linux-based VPN server, and OpenVPN Cloud, a remote access service that allows companies to avoid the costs and maintenance of installing their own servers.
OpenVPN has several benefits over other types of VPN Work. OpenVPN uses one single port to transmit data between client devices and server devices. Because of this, it’s immune to VPN blockages and uses the same Port 443 as SSL. Another benefit of OpenVPN is its ability to use dynamic IP addresses. Unlike many other VPN protocols, OpenVPN allows you to change your IP address whenever you want. If you’re worried about VPN blockage, OpenVPN is the best option.
Authentication & Key Management
IPSec VPN uses cryptographic protocols to establish encrypted communication between two entities. The protocol is based on an Internet Key Exchange (IKE) protocol. ISAKMP defines a standard framework for authentication and key management. In addition to defining the security level, it also provides management and key exchange services. Security associations can be created and used either manually or dynamically. Both directions of communication need two security associations. To implement bi-directional IPSec VPN, two security associations must be established.
An IPSec VPN tunnel is comprised of two devices, called peers. At either end of the VPN tunnel, the peers exchange messages about encryption and authentication. These messages are encrypted and decrypted. When the data exchange is complete, the channels are terminated and the cryptographic keys are discarded. This process is known as phase two. Phase one involves setting up an encrypted connection. Phase two focuses on negotiating the parameters.
Sensitive Data
An SSL VPN Work protects your sensitive data while you are online. This is important because malware attacks usually target browsers. To prevent this, your employees should be educated on how to keep their browsers secure. SSL VPNs are easy to install and use. To keep your information safe, it is important to install antivirus software and install updates regularly. This is not all. There are many other ways that hackers can access your data. Keeping your information safe is a balance between usability and security.
Final Words:
An SSL VPN can also be configured to protect against dictionary attacks. It uses one time keys to validate your identity. The client applications are delivered to your computer by an SSL VPN vendor. Once you’ve installed them, you can access IP-restricted campus resources. SSL VPNs also protect your privacy, so you can enjoy the benefits of secure connections. To learn more about SSL VPNs, read our guide to learn more! But be sure to get started here!



![[pii_email_b4969755ef6881519767] Error Code](https://techdailymagazines.com/wp-content/uploads/2021/09/PicsArt_09-06-12.06.45-390x220.jpg)
![Fixing the PII [pii_email_5b7450b3c52ee3dc0fbe] Error Code](https://techdailymagazines.com/wp-content/uploads/2021/09/PicsArt_09-05-11.28.49-390x220.jpg)